Goals
The intended use of the Global Certificate Chain File (GCCF) and Local Certificate Chain File (LCCF) is to facilitate the distribution of certificates among SCMS components and EEs. Collecting certificate chains into these files will significantly reduce the need for collaborative distribution of certificates. These files will be the primary mechanism to inform components and EEs about new certificates in the system including replacements for components that have been revoked or whose certificates have expired or retired.
Structure
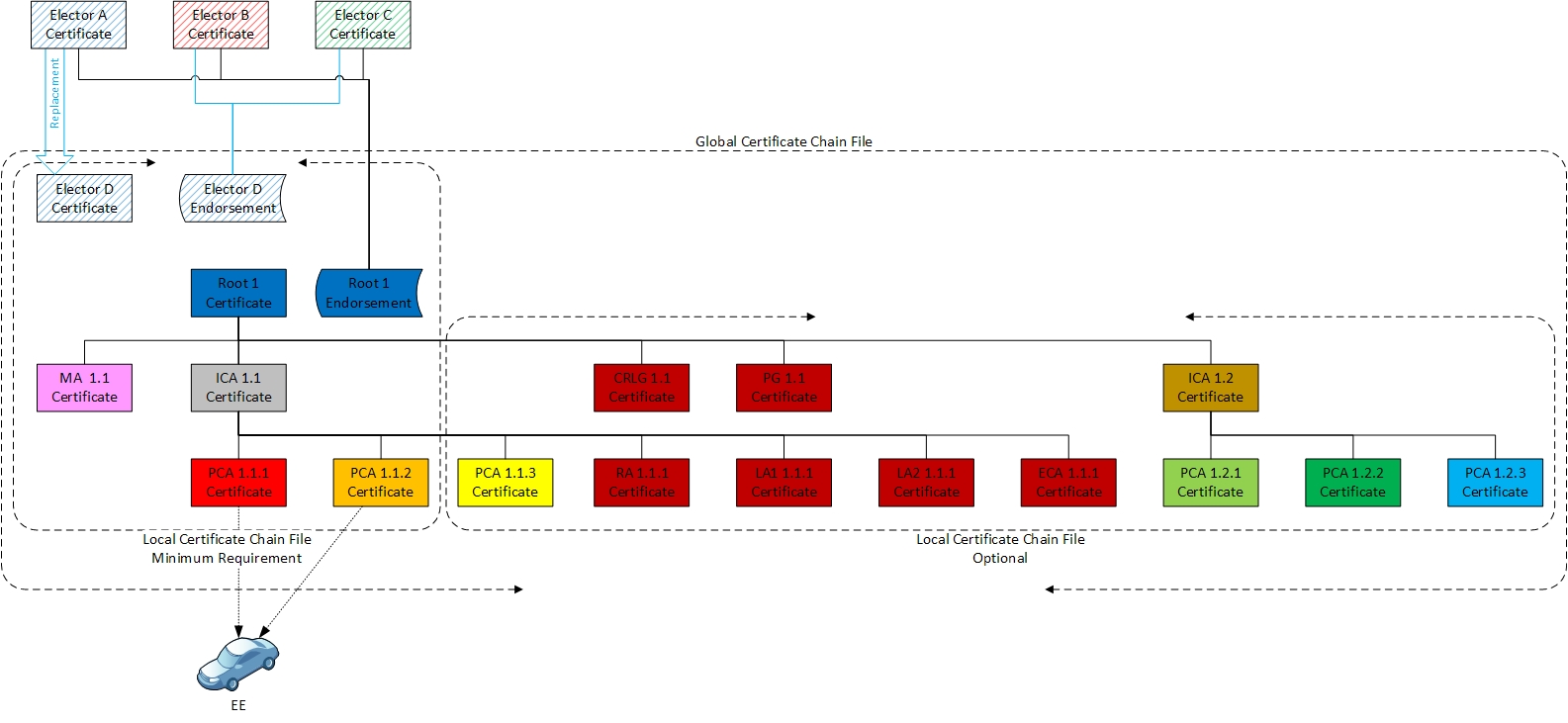
The GCCF shall contain a copy of all SCMS component certificates. It will also contain the root certificate endorsement signed by electors and any elector endorsements for newly added electors. Specifically, it will contain endorsements for all electors' certificates that have been added since the launch of the SCMS and are still valid.
Each RA will create an LCCF that contains, at a minimum, all of the PCA certificate chains that are used to issue pseudonym certificates for its EEs (this is to support P2P certificate distribution) and the SCMS certificates of all components that the EE must interact with or trust (RA, MA, CRLG, Root CA and elector endorsements). Optionally, an RA may choose to provide other PCA certificate chains in the LCCF. Any EE connecting to its associated RA shall get the current LCCF if the RA has a later version than the EE. For the POC, all content in GCCF will be contained in the required section of LCCF and these files will be created manually. The GCCF and LCCF are not signed as each certificate within the file has a signature. The recipient of a GCCF or LCCF must validate all signatures up to a trusted CA prior to trusting certificates in these files.
Example: Let us say for a particular EE, RA uses PCA1 and PCA2 for generating its pseudonym certificates. RA must provide full certificate chains for PCA1 and PCA2 in the LCCF. The RA may choose to provide certificate chains for other PCAs as well.
Using this LCCF, EEs will be able to:
- Validate certificates generated by their PCA
- Respond
to a certificate request in P2P certificate distribution protocol
- Validate certificates signed by any other PCA that the RA included in the LCCF
In order to validate certificates signed by PCAs that were not included in the LCCF, the EE must request the PCA certificate chains from other EEs via collaborative distribution. The EE must validate all PCA certificate chains obtained via collaborative distribution.
Access & Download
To download the LCCF, the EE will retrieve it from an URL defined
in RA - Services View.
The EE will download the files via a HTTP get request, analogous with the mechanism used to download the pseudonym certificate batch files.
Format
The following diagram shows the relationship between GCCF and LCCF. Note that GCCF and LCCF do not contain initial elector or root CA certificates. However, they contain subsequent ballots endorsing elector and root CA certificates, as well as those new certificates themselves.
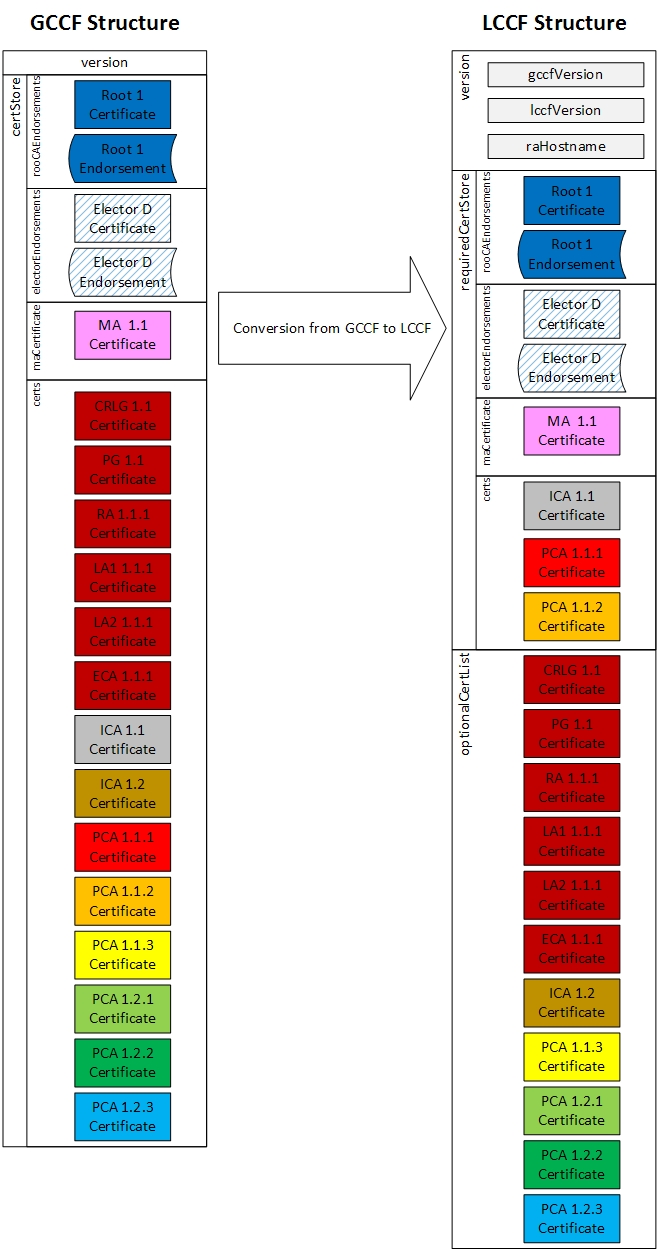
The following diagram shows the structure of GCCF and LCCF.
Global Certificate Chain File (GCCF) Generation:
PG creates the GCCF and makes it available to all RAs whenever there is an update. It shall have the version number for updating purposes. Note that the version numbers are for management purposes only and do not serve any security purpose. The version number is the indicator that the content of the file has changed and is not an indicator of the validity of the content of the file. For the POC, the creation of GCCF is a manual process.
The GCCF structure shall contain the following elements:
| Element | Notes | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| version | This is a 16 bit unsigned integer that represents a unique identifier for this GCCF. It is generated by the PG when the GCCF is published (note that this value is not signed by the PG, it is for informational purposes only). | ||||||||||
| certStore |
This is a structure that holds the following values:
|
Note that for the PoC, the GCCF will contain all certificates for all SCMS components.
Creation of Local Certificate Chain File (LCCF)
The RA creates the LCCF and makes it available to all EEs whenever there is an update. For the POC, the creation of LCCF is a manual process. It is up to OEMs or other authorized RA operators to decide whether they want to use the complete GCCF as their LCCF, or create only a specific, proprietary LCCF using limited, pertinent information from the GCCF.
The LCCF structure shall contain the following elements:
| Element | Notes | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| version |
This is a structure that holds the following values:
|
||||||||||
| requiredCertStore |
This is a structure that holds the following values:
|
||||||||||
| optionalCertList | This is a list of certificates. This list may include any additional certificates that the generating RA chooses to include. It should not duplicate any certificates already contained in the requiredCertStore. |
Note that for PoC, the requiredCertStore will contain the full certificate chains for all PCAs and the optionalCertList will be empty.
Use Cases Affected
- Use Case 1: SCMS Component Setup
- Use Case 2: OBE Bootstrapping
(Manual) and Use Case 12: RSE Bootstrapping
(Manual)
- During bootstrap the device gets all the necessary certificates, ECA, RA, MA and LCCF
- Step 3.3: Initial Download of Pseudonym Certificates, Step 3.5: Top-off Pseudonym Certificates, Step 13.3: Download RSE Application Certificate, Step 19.3: Initial Download of OBE Identification Certificates,
and Step 19.5: Top-off OBE Identification Certificates
- RA provides the updated LCCF
- Use Case 11: Backend Management
ASN.1 Definition
-- (C) Copyright 2017, 2018 Crash Avoidance Metrics Partners LLC, VSC5 Consortium
--
-- Licensed under the Apache License, Version 2.0 (the "License");
-- you may not use this file except in compliance with the License.
-- You may obtain a copy of the License at
--
-- http://www.apache.org/licenses/LICENSE-2.0
--
-- Unless required by applicable law or agreed to in writing, software
-- distributed under the License is distributed on an "AS IS" BASIS,
-- WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
-- See the License for the specific language governing permissions and
-- limitations under the License.
--
-------------------------------------------------------------------------------
-- Certificate Chain Files
--
-- Defines structures for storing and exchanging global and local certificate
-- chain files (GCCF and LCCF). Includes properties for root management
-- messages.
--
-- This file is part of the SCMS protocol developed by CAMP VSC5
-- It depends on the IEEE 1609.2 protocol specification
-------------------------------------------------------------------------------
-- @namespace IEEE1609dot2-cert-chains
IEEE1609dot2-cert-chains {iso(1) identified-organization(3) ieee(111)
standards-association-numbered-series-standards(2) wave-stds(1609)
dot2(2) base(1) cert-chains(4) major-version-2(2)}
DEFINITIONS AUTOMATIC TAGS ::= BEGIN
EXPORTS ALL;
IMPORTS
Hostname,
Time64,
Uint16
FROM IEEE1609dot2BaseTypes {iso(1) identified-organization(3) ieee(111)
standards-association-numbered-series-standards(2) wave-stds(1609)
dot2(2) base(1) base-types(2) major-version-2(2)}
SignedData,
Certificate,
ImplicitCertificate,
ExplicitCertificate
FROM IEEE1609dot2 {iso(1) identified-organization(3) ieee(111)
standards-association-numbered-series-standards(2) wave-stds(1609)
dot2(2) base(1) schema(1) major-version-2(2)}
ElectorBallot
FROM Ieee1609Dot2ScmsComponentCertificateManagement
{iso(1) identified-organization(3) ieee(111)
standards-association-numbered-series-standards(2) wave-stds(1609)
dot2(2) scms(4) interfaces(1) component-certificate-management(3) major-version-2(2)}
;
---
-- @brief The CertificateChainFiles is the parent message type for enclosing
-- all types of certificate chain files transferred between SCMS
-- components.
-- @class CertificateChainFiles
-- @param globalCertificateChainFile contains the global certificate chain.
-- @param localCertificateChainFile contains the local certificate chain.
CertificateChainFiles ::= CHOICE {
globalCertificateChainFile GlobalCertificateChainFile,
localCertificateChainFile LocalCertificateChainFile,
...
}
---
-- @brief This data type contains the full certificate of all SCMS components.
-- This file is signed by the Policy Generator.
-- @class GlobalCertificateChainFile
-- @param version is the unique version number for this GCCF.
-- @param certStore is the list of certificats and all issuers.
-- @see Uint16
GlobalCertificateChainFile ::= SEQUENCE {
version Uint16,
certStore CertificateStore,
...
}
---
-- @brief This data type contains a minimum set of full certificates as
-- required by policy and the selection of the local RA that generated
-- this file. This file is signed by the Policy Generator.
-- @class LocalCertificateChainFile
-- @param version is the composite version for this file.
-- @param requiredCertStore is the required list of certificates.
-- @param optionalCertList is the list of optional certificates.
-- @see Certificate
LocalCertificateChainFile ::= SEQUENCE {
version CompositeVersion,
requiredCertStore CertificateStore,
optionalCertList SEQUENCE SIZE(0..MAX) OF Certificate,
...
}
---
-- @brief This data type contains the version numbers of each type of
-- certificate chain file.
-- @class CompositeVersion
-- @param gccfVersion is the GCCF version that was used to generate this file.
-- @param lccfVersion is the unique local version for this LCCF.
-- @param raHostname is the name of the RA that generated this LCCF.
-- @see Uint16, Hostname
CompositeVersion ::= SEQUENCE {
gccfVersion Uint16,
lccfVersion Uint16,
raHostname Hostname
}
---
-- @brief A certificate store is a list of root and elector endorsements plus
-- lists of ICA and PCA certificates needed by EEs to validate message.
-- This base type is used to construct the GCCF and the LCCF. The PG
-- creates the GCCF by assembling all certificates needed to validate
-- all EE certificates in the SCMS. An RA creates the LCCF by pruning
-- the GCCF down to the lists needed by the EEs that are assigned to
-- that RA. Note that these are lists of certificates, not certificate
-- chains as defined in 1609.2. The primary reason for not using a list
-- of certificate chains is to eliminate redundancy. If we used a list
-- of certificate chains, each chain would have a copy of the same root
-- CA and some chains would have copies of the same ICA.
-- @class CertificateStore
-- @param rootCAEndorsements are optional for as long as the SCMS OPs project
-- does not have Electors. As soon as they are
-- introduced, a minimum of 1 rootCAEndorsement is
-- required.
-- @param electorEndorsements are required by the SCMS components (including
-- EEs) to validate non-expired certificates before
-- adding a new Elector and storing new elector
-- certificate in the certificate store.
-- @param maCertificate is the MA certificate.
-- @param certs is a list of cerificates of all other SCMS
-- components.
-- @see Certificate
CertificateStore ::= SEQUENCE {
rootCAEndorsements SEQUENCE SIZE(0..MAX) OF ElectorBallot,
electorEndorsements SEQUENCE SIZE(0..MAX) OF ElectorBallot,
maCertificate Certificate,
certs SEQUENCE SIZE(0..MAX) OF Certificate,
...
}
END